Articles by Rouven Czerwinski
Wir haben doch etwas zu verbergen: Schlüssel mit OP-TEE verschlüsseln
Moderne Linux Systeme müssen häufig zwecks Authentifizierung bei einer Cloud- basierten Infrastruktur oder einer On-Premise Maschine eigene kryptografische Schlüssel speichern. Statt der Verwendung eines Trusted Platform Modules (TPM), bieten moderne ARM Prozessoren die TrustZone-Technologie an, auf deren Basis ebenfalls Schlüssel oder andere Geheimnisse gespeichert werden können. Dieses Paper zeigt die Nutzung des Open Portable Trusted Execution Environments (OP- TEE) mit der Standardkonformen PKCS#11 Schnittstellen und i.MX6 Prozessoren von NXP als Beispiel.
Using OP-TEE to Authenticate IoT Devices
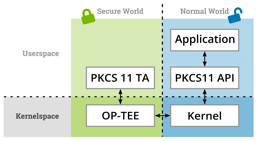
Deploying IoT devices into the field poses the question of how to authenticate these devices against your own services. While software authentication of bootloader, kernel, and filesystems ensures that only trusted software is run on the device, preventing extraction of authentication data from the device requires the use of a Trusted Platform Module (TPM) or equivalent mechanisms. This blog post introduces OP-TEE and PKCS#11 as a software alternative.
Porting Barebox to the Digi CC-IMX6UL SBC Pro
One of our projects required the addition of board support for the Digi ConnectCore 6UL SBC Pro to the Barebox bootloader. This article outlines the used development setup and required additions to the bootloader to support a board with a well supported processor. Development of the board support was done live during the monthly talks at Stratum 0, the hackerspace in Braunschweig. The video (in German) is embedded at the end of the article.