RAUC v0.2 Released
We proudly just sent out a new release of the RAUC update framework.
With 171 individual changes since v0.1.1 we have put much effort in enhancing both the usability and the stability of RAUC while adding a set of useful features making RAUC applicable for even more use cases.
Scroll through the following list to get an overview of the most significant changes for this release:
For those who use RAUC from the command line, the tool now provides an output of the installation progress as well as improved error reporting to ease quickly finding configuration or runtime issues.
RAUC now supports splitting up the installation and the actual activation of an update. This can be quite useful for scenarios where you first want to roll out updates to all devices in the field and then enable it for all devices together at a defined point in time.
Therefore both the system configuration option activate-installed as well as new D-Bus method mark along with the new rauc status mark-active sub command were introduced.
The changes not only allow to handle delayed activation but also enable you to use the RAUC bootloader abstraction to modify the target to boot, e.g. for testing.
When dealing with certificates, you might have asked yourself often in the past if you signed your update correctly, if the verification works as expected, etc.
Now, the RAUC commandline tool provides features and options to ease dealing with certificate debugging:
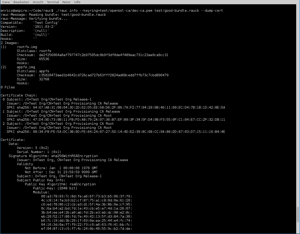
A newly introduced --keyring argument allows you to directly define the keyring to use for verification without the need to have a system.conf file. This is especially useful for inspecting bundles on your build host.
The output of rauc info now dumps the trust chain (with subject, issuer, and calculated SPKI (SubjectPublicKeyInfo) hash) successfully verify the inspected bundle.
If passing the newly introduced --dump-cert argument, you will also get the full signer cert of the bundle printed.
But, debug printout is not the only improvement targeting certificate support:
When scrolling through the help text of the RAUC tool, you may encounter a fully new command rauc resign. We finally added (after we've already mentioned it in the documentation) support for resigning bundles. This can be quite useful when changing a bundle (after having tested it successfully) from development/testing state to production state without actually having to touch its well-proven content anymore.
RAUC resign allows you to verify the bundle on your build host, remove the signature and add a new one created from a different key.
Last but not least, a significant effort we've put in enhancing the documentation, as you could already read in this blog post.
For an extended list of all changes (especially the bugfixes) contained in the v0.2 release, see the CHANGES file.
For the next release we already have a bunch of new features planned or already prepared, including a central comprehensive status file for storing slot checksum and metadata, support for placing and honoring intermediate certificates in bundles, streaming support based on casync and much more.
Further Readings
You can buy RAUC and labgrid sponsor packages now
RAUC and labgrid are open source software projects started at Pengutronix, that are quite successful in their respective niche. Starting today you can buy sponsorship packages for both projects in the Linux Automation GmbH web shop, to support their maintenance and development.RAUC v1.15 Released
It’s been over half a year since the RAUC v1.14 release, and in that time a number of minor and major improvements have piled up. The most notable change in v1.15 is the newly added support for explicit image types, making handling of image filename extensions way more flexible. Other highlights include improved support for A/B/C updates and several smaller quality improvements. This release also includes the final preparations for upcoming features such as multiple signer support and built-in polling.
RAUC - 10 Years of Updating 🎂
10 years ago, almost a decade before the Cyber-Resilliance-Act (CRA) enforced updates as a strict requirement for most embedded systems, Pengutronix started RAUC as a versatile platform for embedded Linux Over-The-Air (and Not-So-Over-The-Air) updates.