RAUC v1.3 Released
Here it is, commit number 1700, 291 commits after the v1.2 tag: The v1.3 release of RAUC is out in the wild and adds a lot of new and useful features together with some fixes.
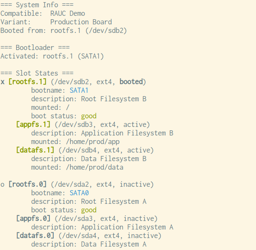
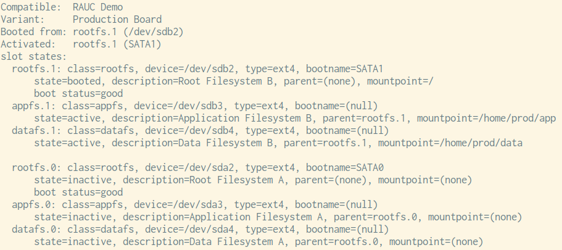
We start with the most 'visible' feature: When invoking the command line tool rauc status you will notice a reorganized output. This provides a colored output (with optional UTF-8 character support) along with a changed layout that should make it easier to identify the system status.
With a new D-Bus API method for starting an installation, we have eliminated a significant drawback of the initial API design that made it impossible to pass optional arguments when installing. For example, this now makes the long-existing --ignore-compatible option available in all scenarios but will also enable potential new install options like a --dry-run in the future.
Bundle Signatures
A few notable improvements to bundle signing landed in RAUC 1.3. By default, RAUC does not check the certificate's key usage attributes. When the bundle signing certificates are part of a larger, shared PKI, RAUC can now require specific purposes like codeSigning, thereby allowing better policy enforcement via the PKI. Checking of key usage attributes can be enabled with the check-purpose configuration option:
[keyring]
path=/path/to/ca.cert
check-purpose=codesign
Also, you can now require checking of CRLs during installation (which is disabled by default in OpenSSL). Setting the check-crl configuration option changes this:
[keyring]
path=/path/to/ca.cert-with-crl
check-crl=true
If the keyring already contains a CRL, but checking is not enabled, a warning will now be printed.
For bundles with expired certificates, you can now use the --no-verifiy option for rauc resign to easily create a fresh signature.
As the OpenSSL project dropped support for all version before 1.1.1, we have now removed support for those as well. If you still use a deprecated and thus insecure OpenSSL version, this is the time to upgrade!
Further Enhancements
A couple of limitations in bundle and image size handling RAUC had when running on a 32 bit system were removed.
For those running on very constrained systems, some options for reducing the size of the RAUC binary were added.
If you want to customize bundle creation, this version adds some options for that: --mksquashfs-args="-option-to-add" for mksquashfs, and --casync-args="--another-option" for casync.
A couple of minor bugs and memory leaks were fixed, especially an error reporting bug that may have triggered during bundle verification if an invalid keyring was configured which lead to a non-intuitive error message "rauc-ERROR **: Not enough substeps: check_bundle".
Testing
The main test suite was previously run in UML (User Mode Linux), but this turned out to be difficult to support in the various build environments. This was now replaced by running a normal kernel in QEMU to better decouple it from the host system and kernel while preparing CI testing of more areas, like NAND writing support via the kernel's nandsim module.
Thanks to all contributors since v1.2: Arnaud Rebillout, Christopher Obbard, Enrico Jörns, Jan Kundrát, Jan Lübbe, Louis des Landes, Marco Felsch, Martin Hundebøll, Michael Heimpold, Michael Tretter, Rasmus Villemoes, Rouven Czerwinski, Trent Piepho, Ulrich Ölmann
Further Readings
You can buy RAUC and labgrid sponsor packages now
RAUC and labgrid are open source software projects started at Pengutronix, that are quite successful in their respective niche. Starting today you can buy sponsorship packages for both projects in the Linux Automation GmbH web shop, to support their maintenance and development.RAUC v1.15 Released
It’s been over half a year since the RAUC v1.14 release, and in that time a number of minor and major improvements have piled up. The most notable change in v1.15 is the newly added support for explicit image types, making handling of image filename extensions way more flexible. Other highlights include improved support for A/B/C updates and several smaller quality improvements. This release also includes the final preparations for upcoming features such as multiple signer support and built-in polling.
RAUC - 10 Years of Updating 🎂
10 years ago, almost a decade before the Cyber-Resilliance-Act (CRA) enforced updates as a strict requirement for most embedded systems, Pengutronix started RAUC as a versatile platform for embedded Linux Over-The-Air (and Not-So-Over-The-Air) updates.